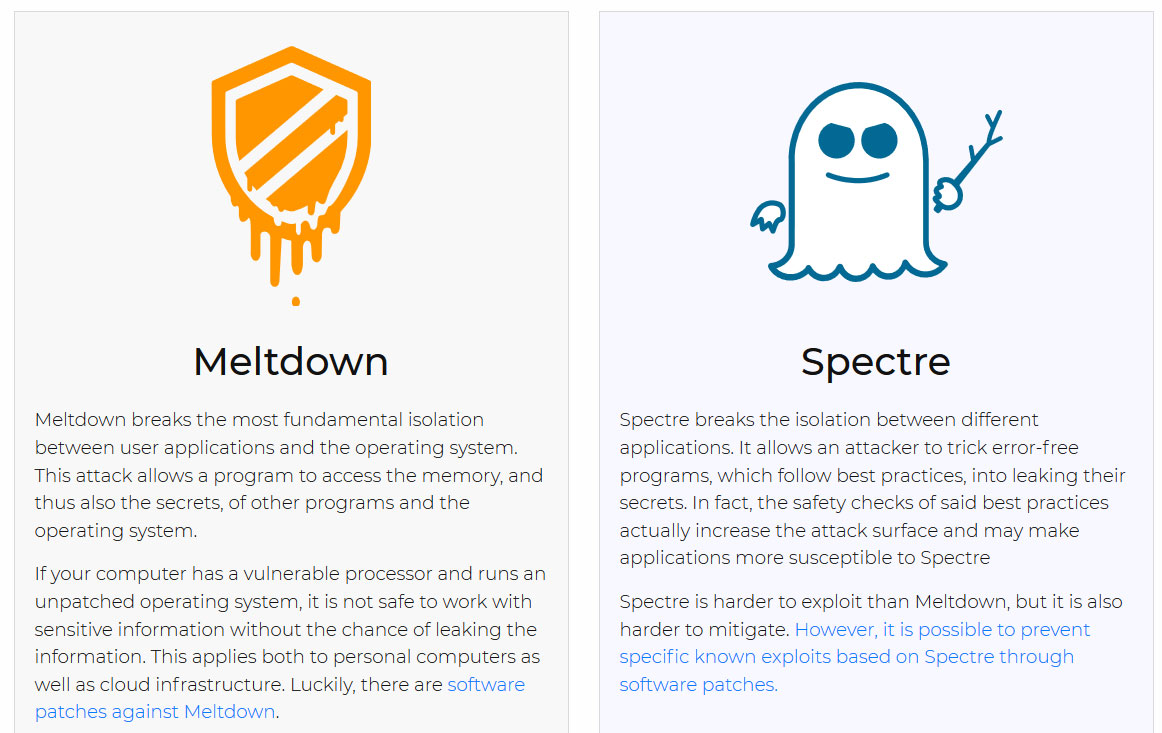
The recent Spectre and Meltdown vulnerabilities have created a great deal of uncertainty and questions about whether and how they affect software such as that provided by Open-Xchange. The vulnerabilities are complex and subtle in terms of how they can be exploited, but in terms of how OX software and services (OXaaS) are affected, the following statements should help to understand the impact.
OX Software - Both Spectre and Meltdown rely on the ability to run “untrusted” (i.e. controlled by the attacker) code on a host. OX Software, including AppSuite, Dovecot and PowerDNS does not provide a mechanism for untrusted code to run on the servers which host that software. Thus attackers cannot access information stored in the memory of servers running OX software solely by using the Spectre or Meltdown vulnerabilities.
OXaaS - Spectre/Meltdown do provide a possible attack vector for Virtual Machines under the control of an attacker to access information about other Virtual Machines hosted on the same physical server. This particular scenario is applicable in a public cloud infrastructure, however OXaaS runs in a completely private cloud infrastructure, where all Virtual Machines are under the control of Open-Xchange and thus there is no ability for attackers to gain access to the memory of such servers solely by using Spectre or Meltdown.
It should be noted that the various workarounds/fixes (particularly the Kernel Page Table Isolation patch (KPTI)) for Spectre and Meltdown almost certainly will have some performance impacts for software, including OX Software. The impact of these will vary over time. Early measurements for PowerDNS Recursor server indicate a potential 10% performance impact for example, which seems to be matched by other reports, but over time as the workarounds evolve, they may become less performance impacting.
It is up to customers whether they actually install (or enable) workarounds for Spectre/Meltdown, including the KPTI patch. For example, customers using completely private compute environments, who are sure that there is no way to run untrusted code on those servers, may feel that the performance slowdown is not worth it; however every environment should be evaluated on its own merits. According to the following blog by Google, they have implemented the KPTI patch on all their production servers, with negligible impact on performance.